
Threat Intelligence Program Development
For organizations that are ready to make strategic investments in security and proactively protect their brand, employees, and assets. Go beyond having an Information Security Program and develop a true Enterprise Threat Intelligence Program that serves the entire organization.
The Problem
Reactive, Autonomous, Mutually Exclusive Security Functions

Reactive. Organizational “security programs” are predominantly reactive – protecting and defending in response to an active threat. Even “proactive” actions are essentially related to an indicator of compromise (IoC), which means someone else was affected and shared details allowing others to react, thereby avoiding the same fate.
Autonomous. Typically, security teams operate independently and autonomously, being organizationally stove-piped, segregated, and minimally collaborative. The better solution, described below in detail, is a Threat Intelligence Program that creates a holistic security culture within the organization’s ecosystem.
Mutual Exclusion. Technology has blurred the lines between security domains once thought to be mutually exclusive security functions. Organizations are unwilling or unable to create a true security ecosystem unified under a single program that proactively anticipates, detects, deters, delays, and destroys threats.
The Solution
An Enterprise Threat Intelligence Program

An Enterprise Threat Intelligence Program is multi-faceted. It strategically supports the organization’s business objectives by simultaneously reducing risk, improving the security posture, and protecting its brand, employees, assets, and intellectual property.
An Enterprise Threat Intelligence Program:
- Is business objective driven
- Enriches C-suite decision making
- Reduces risk and helps minimize loss
- Functions at all organizational levels: strategic, operational, and tactical.
- Anticipates threats, searching for early warning signs of malice – indicators of (potential) attack (IoA) – instead of waiting for a neighbor to (hopefully) share indicators of compromise (IoC).
- Transforms formerly stove-piped security functions from reactive to proactive, autonomous to collaborative, mutually exclusive to interdependent.
An Enterprise Threat Intelligence Program is multi-faceted. It strategically supports the organization’s business objectives by simultaneously reducing risk, improving the security posture, and protecting its brand, employees, assets, and intellectual property.
An Enterprise Threat Intelligence Program:
- Is business objective driven
- Enriches C-suite decision making
- Reduces risk and helps minimize loss
- Functions at all organizational levels: strategic, operational, and tactical.
- Anticipates threats, searching for early warning signs of malice – indicators of (potential) attack (IoA) – instead of waiting for a neighbor to (hopefully) share indicators of compromise (IoC).
- Transforms formerly stove-piped security functions from reactive to proactive, autonomous to collaborative, mutually exclusive to interdependent.
The Solution
An Enterprise Threat Intelligence Program

Benefits

- Reduced risk by identifying threats in their pre-attack phases
- Reduced cost by reducing the time, money, and manpower spent on incident response
- Reduced cost by reducing man hours spent on incident management because threats are found and addressed in advance
- Consistently provide reliable, actionable information for C-Suite and other decision makers
- Add value internally by providing information that enables critical adaptation of business operations
- Add value externally by providing threat intelligence that allows others to make well-informed business decisions
Benefits

- Reduced risk by identifying threats in their pre-attack phases
- Reduced cost by reducing the time, money, and manpower spent on incident response
- Reduced cost by reducing man hours spent on incident management because threats are found and addressed in advance
- Consistently provide reliable, actionable information for C-Suite and other decision makers
- Add value internally by providing information that enables critical adaptation of business operations
- Add value externally by providing threat intelligence that allows others to make well-informed business decisions
Divine Intel will help your organization develop a comprehensive Enterprise Threat Intelligence Program and work with key stakeholders to ensure their intelligence needs are identified and implemented.
As we work with you to build out your program, we help you avoid mistakes and identify your unique resource requirements to include what to look for when hiring.
We design your custom Enterprise Threat Intelligence Program that will grow as you grow, leveraging the talent you have and identifying the talent you will need. While every client is unique, each program is designed to incorporate core threat intelligence functions:
1. Planning & Governance
2. Data Collection
3. Data Processing
4. Analysis
5. Evaluation
6. Collection Tuning
7. Dissemination & Reporting
8. Action & Feedback
Resource: for more information, read our blog Outlining a Threat Intelligence Program.
Program Content
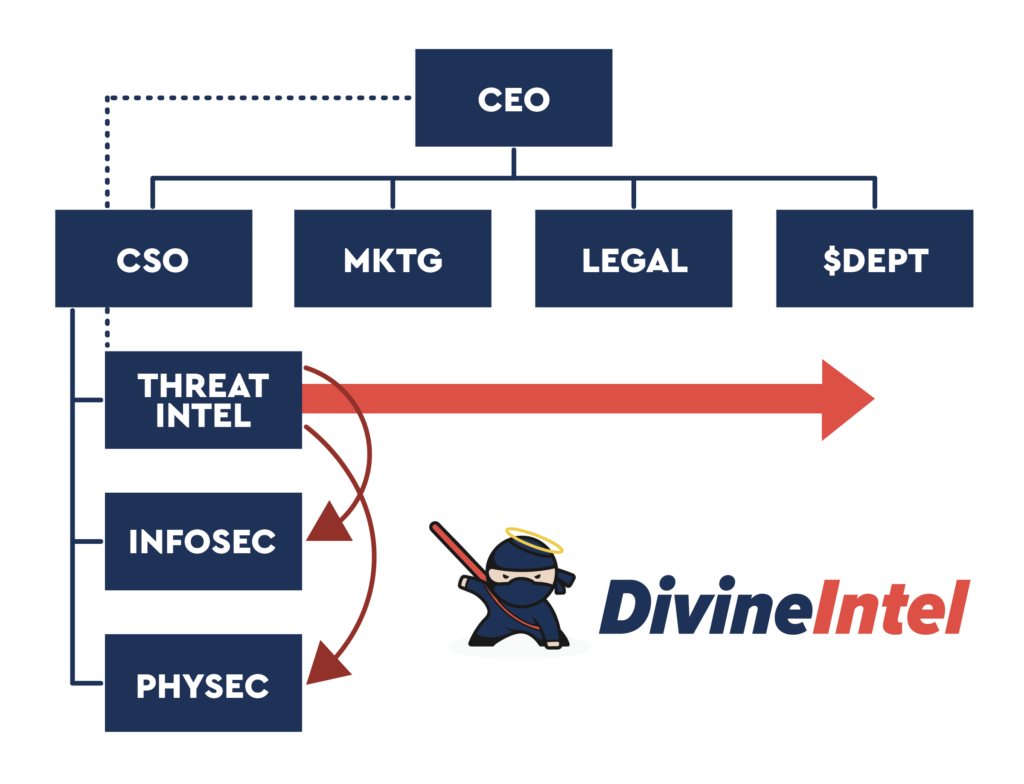
Threat Intelligence
Program Content

To answer this question, let’s take a look at one of the largest organizations that successfully leverages threat intelleigence, the Unites States military, and how its structure and functions commpare to commercial corporations.
Military commanders, even at the lowest strategic level, equivalent to a CEO, have the same basic staff functions at an enterprise level supporting them in achieving a mission. These staff roles are typically identified numerically as G1-4, and G6, and they are as follows: G1 is Human Resources; G2 is Intelligence; G3 is Operations; G4 is Logistics; G6 is Information Technology; and he has the commanders under him that perform the other necessary functions to succeed depending on the type of unit.
In order for the commander to stay abreast of threats to his unit, he relies on threat intelligence and situational awareness reports from his Intelligence Team. All persons performing intelligence collection, processing, analysis, evaluation and reporting, fall under the senior leader of the Intelligence shop. They serve up, across, down and outside of the organization.
First and most importantly they serve the Commander, providing him with intelligence information so that he may make well-informed decisions. In the corporate world, this can be anything from information about a potential acquisition, to a new phishing threat targeting C-levels or threat scenarios the organization should prepare for.
They also serve across by providing intelligence information not only to the Commander, but also to the Operations, Information Technology, & Logistics departments. They also serve down the organization by passing threat/intelligence information down to the other commanders relevant to functions they perform or areas in which they are operating, equivalent to our Marketing or Sales departments.
Finally they serve outside their immediate organization by sharing and collaborating on intelligence with other agencies and allied forces, equivalent to our industry partners and other threat intelligence teams or special interest groups.
