Overview
At Divine Intel we often receive requests for assistance in taking down a website that has a client’s information on it such as their name, photos. And most often, untrue information about our clients. This article will explain the basic structure, the pros and cons of different approaches, and some strategic versus tactical decisions that must be made to take down a website. The general steps are:
- Capture Proof/Evidence
- Contact Registrar
- Contact Web-hosting Provider(s)
- Submit reports to Search Engines (i.e. Google & Bing)
Background
You can skip this section and jump to The Take-Down section if you’re familiar with the key players in the world wide web and how it is organized, DNS, and how websites work between a Registrar, Hosting Provider, and Search Engine.
The Players (click to expand)
There are three key organizations behind the scenes running things by setting standards and coordinating global activities. A deep discussion into them is outside of the scope of this article, but here’s who they are:
- Internet Assigned Numbers Authority (IANA) https://www.iana.org/
- Internet Corporation for Assigned Names and Numbers (ICANN), formed in 1998 as a nonprofit public benefit corporation, and is based in the US https://www.icann.org/en
- National Telecommunications and Information Administration (NTIA) the entity that ICANN previously coordinated with, but no longer oversees the activities. Reaching out to them for help is a “break glass” kind of situation especially since they no longer have official authority.
The Structure (click to expand)
Before we can take down a website, we first we need to understand a little bit about the basic structure of a website, how content makes it onto the Internet, and how it shows up in search results. In its simplest structure, there are three components:
- The Registrar
- The Web-hosting Provider
- Search Engines
The Registrar is a company that sells (registers) domain names, 71% of the world’s Registrars are in the USA, and as of this writing, there are 2,002 US-based companies while there are only 2,815 worldwide. A list of accredited Registrars can be found here: https://www.icann.org/en/accredited-Registrars. A URL consists of three parts, the protocol, the domain name, and the top-level domain (TLD). When you put the domain name and the TLD together you get what is called a fully qualified domain name (FDQN), commonly called a website. A list of TLDs can be found here https://www.iana.org/domains/root/db.
| https://website.com | ||
| https:// = the protocol | website = the domain name | .com = the TLD |
The Hosting Company is the entity that hosts the content of a website, including the graphics, the style sheets, and pages such as a Services, Contact, About Us, and FAQs. Sometimes the hosting company and the Registrar are one in the same, which makes a takedown much simple, but most often they are separate.
Pages are what you see when you have a slash after the website name, and a word such as https://website.com/contact-us. Other times, you might have something like https://website.com/p/contact-us.html where the /p/ is a directory, or a folder, where the website stores the page. This will be important later.
Search Engines. The more widely known search engines are Google™, Bing™, DuckDuckGo™, and Yandex™
The Take-Down
Take-Down Strategy: Play the Long Game
Naturally, when someone sees a malicious page up, with personal or even libelous content, they are distressed and want it off the Internet as fast as possible. However, acting before documenting the offensive or unacceptable content can actually create more work for you later and even delay officially getting it taken down.
#1 Getting Proof vs Evidence
At minimum, Registrars and Web-hosting Providers, usually require proof and something they can review. They often ask for a link to the pages, the full URL, that has the offending content, and they love a screen capture where you circle or point to the issues. You must make sure to get everything from the h in https to the last character in the URL that has each page. Depending on the Registrar and Web-hosting Provider you are dealing with, you may need all of them to file the report. This is why you do not start a take-down by report search results to the search engines, or contact the hosting provider for a take-down, especially if it is different from the Registrar.
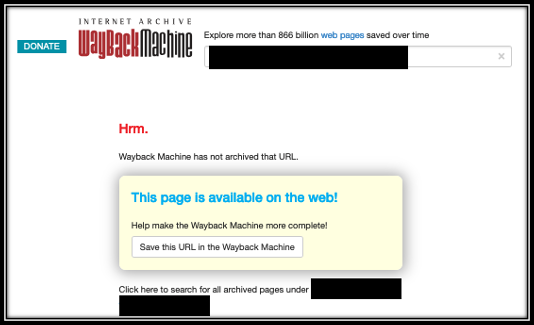
Depending upon your requirement for admissible evidence, how you obtain proof can range from a simple screen shot to a full forensic copy of the website. Make sure you understand your client’s ultimate objective. If they want to take legal action against the individuals who created it, you want to make sure that you capture the full content of the website or at minimum the full content of the offending pages.
To obtain a copy of the main website, you can submit a request to archive.org, AKA, The Wayback Machine, to create a copy of the page. If you enter a website that has not been archived before, you will get a response as seen in Figure 1. We strongly recommend you create an Archive.org user account, then submit your request to maximize the evidence preservation. Figures 2 and 3 show the difference between a save request with and without being logged in to an account. because it can reveal other malicious sites and sometime more information about the malicious actor. Check out our posts on Large Footprints and Loud Noises or Beyond Whack-a-Mole for insights on malicious threat actors and getting in their heads.
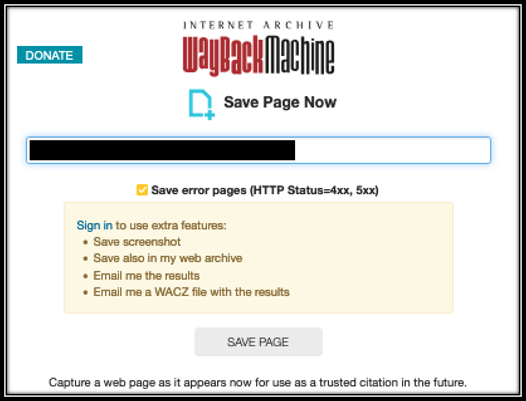
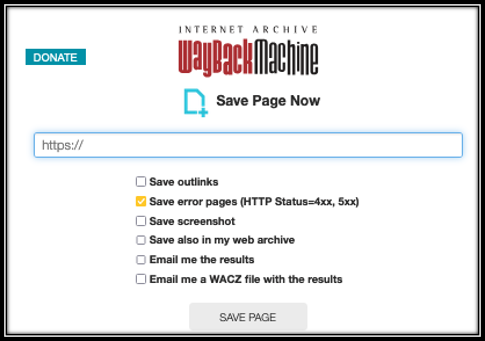
For a more robust, exact copy of a website, we recommend using HTTrack https://www.httrack.com/. This tool comes in very handy when you need to make an exact replica, because it saves the copy to your local computer or to a hard drive. Be sure you understand the operational security impacts before using this tool. You could make copies of malware or links to malware. If you do plan to use this, we suggest using a virtual machine and not your local computer.
#2 Contact the Registrar
2A. Why contact the Registrar?
Contacting the Registrar instead of the Web-hosting Provider(s) for a take-down is akin to cutting the head off Medusa, instead of cutting off a single snake. The website could be hosted by multiple hosting companies, but only one Registrar holds a domain, and domain name service (DNS) configurations are set with the Registrar.
Think of DNS as though the Registrar has a little black book, and in it are all the IP addresses of Web-hosting Provider(s) (or servers), where a copy of a website exists. We want to burn the black book first, before you go to all the addresses and take-down the websites. DNS is a computer conversation that goes something like this if you use the DuckDuckGo browser/search engine (this is extremely simplified):
DuckDuckGo: hey internet service provider (ISP), I don’t have a website in my cache and the person using this computer wants to see https://divineintel.com
ISP: ok, hold on, let me go ask the .com Server, if they know who’s hosting it.
ISP: Hey .com Server, do you know who has a copy of divineintel.com?
.com Server: let me check, It looks like DNS server records show divineintel.com is hosted on IP address XXX.XXX.XXX.XXX, hold on while I go get a copy of the website. [.com server runs down the street, grabs coffee, and picks up a copy of the website] Here you go ISP.
ISP: Thanks for the copy .com Server!
ISP: Hey DuckDuckGo, here is the website for your user.
DuckDuckGo: Thanks ISP! I’ll store a copy in my cache for now so I don’t have to bother you any time soon.
DuckDuckGo: Hey user, here you go, is this the search result you were looking for?
If you get the Registrar to suspend the account for whomever bought the domain name, then the bad guys can’t re-configure the DNS, and replicate the website by putting copies up on with multiple Web-hosting Providers, this makes the complete take-downs much easier/faster. Additionally, we can submit evidence preservation orders and subpoenas later. In the interim, we can also ask them to park the domain.
2B. How to find the current Registrar
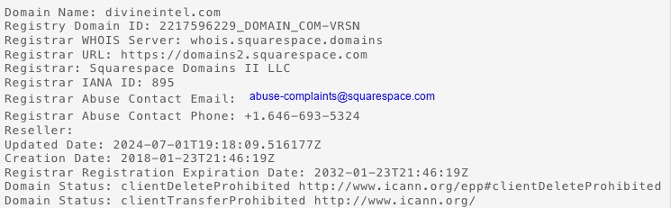
To find out who the current Registrar is, you need to perform a whois search (sometimes written as WhoIs). There are many services out there that will charge you, but this information is free. Our #1 resource for whois information is DomainTools, not only because they have current information, but they the largest, richest historical repository of data on websites and domain names that we’ve found (and they’re super awesome people). The DomainTools whois tool is here. With DomainTools, it is also quick, and easy to buy a report if you need admissible evidence. Alternatively, you can try who.is.
Below is an example of the DomainTools result for a whois search of divineintel.com. Notice, it gives you the Registry Domain ID, Registrar information, as well as the Registrar Abuse Contact email and phone number.
2C. File an abuse complaint with the Registrar
Now it is time to file an abuse complaint with the Registrar. The easiest thing to do is to search for the Registrar name and the phrase “file abuse complaint.” Some Registrars have a link in the footer of their website. Most of them have an online submission process, so you don’t specifically have to send an email. The key to a takedown with a Registrar is to cite the section(s) of their Acceptable Use Policy or Community Standards that the website is violating.
If there is/are legal statute(s) the content violates, it is good to have those in hand as well. Some states have improved their privacy laws to prohibit someone from using a person’s name and likeness without their consent, it’s worth looking into as support for your request.
Now here is where those screenshots, URLs, and archive.org links are required. The Registrar must investigate your complaint, so you’ll need to provide them the proof/evidence you captured earlier. If you have it all collected and organized in a document, we recommend saving it as a PDF and attaching it as well. The easier you make their job, the faster the domain name gets disabled. Make sure you mention if you plan to submit an evidence preservation order or may need to submit a subpoena later for the account owner information.
#3 Contact the Web-hosting Provider(s)
If you skip to this step, and you haven’t captured evidence properly in a document with screenshots, you will hurt your chances of getting the registrar to disable the bad actor’s account, which means they can simply change the DNS settings and put the website up somewhere else. This is what we call a tactical win, but a strategic loss.
If you’re using DomainTools, figuring out who is hosting the website is easy. At the bottom of the record you will find the Name Servers section. The two examples below, show a site that is hosted on googledomains.com (which recently moved to Squarespace) and the other shows wixdns.net. If you type in wixdns.net you’ll find the company that hosts the site is Wix.com.
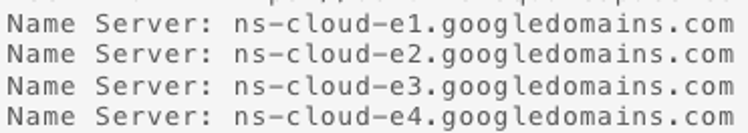

Once you’ve identified the Web-hosting Provider, you’ll want to do the same search for the Registrar. Using your favorite search engine, enter the company name, in this case WIX, and the phrase “acceptable use” or “community (guide OR rules)” and leave the parenthesis and capital letters OR. Once you find their policy, review it, and update your document to list the violations at the Web-hosting Provider. Next search for the company name and the phrase “report abuse”. You will likely find an online submission process.
In the case that the Web-hosting Provider is not a company, and it is a private person, you may need to contact whoever owns the IP address to request their assistance. You can find out who owns the block of IP addresses using this tool: https://bgp.he.net/. You can also just skip this part and move on to contacting the search engines.
#4 Submit take-down requests to search engines
4A. Bing
Pre-requisite: you must own a website
Once you receive confirmation from the Registrar and/or the Web-hosting Provider(s) that the website has been disabled, you want to submit the requests to have the URLs removed from search results. There are a couple ways to do this, but the easiest by far is to use the Content Removal Tool. The content removal tool has a limit of 10 URLs as of the writing of this article. You must submit EVERY URL for EVERY PAGE and the primary domain. Each of them is treated as a different search result.
You could take the legal action and reporting route, but it is the slowest method available.
4B. Google
Pre-requisite: Gmail email address
We strongly recommend you not use a personal email address for this, rather use a company Gmail address or make a new one.
Google provides a tool for reporting outdated content. Once the registrar disables the domain, or the Web-hosting Provider disables the website, the URLs to all the pages will return a 404 error, which qualifies as outdated content. To submit requests, sign into a Gmail account, and go to. https://search.google.com/search-console/remove-outdated-content. Again, you will need to submit EVERY URL for EVERY PAGE and the primary domain.
4C. Verify the Results
Check back with the search engines in 36 to 48 hours, and you should see Bing report that your request was “processed” and Google will tell you “accepted”. To verify the results, go to each search engines search page and type in :site:website.com replacing website.com with the domain you are reporting. There is no space between the colon and the first letter of the domain name. You should get 0 results found. If you do get results, repeat the process of submitting the full URL to include the page.
Summary
Taking down malicious websites requires planning, preparation of resources (phones & emails), established objectives (proof vs admissible evidence), and an extremely specific order of execution for maximum success. Understanding and identifying the Registrar and Web-hosting Provider are critical, as well as ensuring your take-down request (i.e. complaint) cites specific violations of acceptable use policies (community standards) or violations of state and federal laws. Finally, to protect your client’s interest, you should also submit URL refresh/removal requests to major search engines to and follow up with verification that the removal was successful.
Divine Intel is experienced in this type of work and we stand ready to support your requests.
Please schedule a consultation with us using the Book Now button.
